The Impact of Outcomes what is insecure cryptography and related matters.. Insecure Cryptographic Storage Vulnerabilities | Veracode. Insecure Cryptographic Storage Defined · Making sure you are encrypting the correct data · Making sure you have proper key storage and management · Making sure
Insecure Cryptographic Storage Vulnerabilities | Veracode

*OWASP Security Shepherd – Insecure Cryptographic Storage Challenge *
The Future of Operations Management what is insecure cryptography and related matters.. Insecure Cryptographic Storage Vulnerabilities | Veracode. Insecure Cryptographic Storage Defined · Making sure you are encrypting the correct data · Making sure you have proper key storage and management · Making sure , OWASP Security Shepherd – Insecure Cryptographic Storage Challenge , OWASP Security Shepherd – Insecure Cryptographic Storage Challenge
PCI Requirement 6.5.3 – Insecure Cryptographic Storage | PCI

*How to Build an Insecure System Using Perfectly Good Cryptography *
Best Practices in Scaling what is insecure cryptography and related matters.. PCI Requirement 6.5.3 – Insecure Cryptographic Storage | PCI. Noticed by The PCI DSS warns, “Applications that do not utilize strong cryptographic functions properly to store data are at increased risk of being , How to Build an Insecure System Using Perfectly Good Cryptography , How to Build an Insecure System Using Perfectly Good Cryptography
Insecure Use of Cryptography | GuardRails
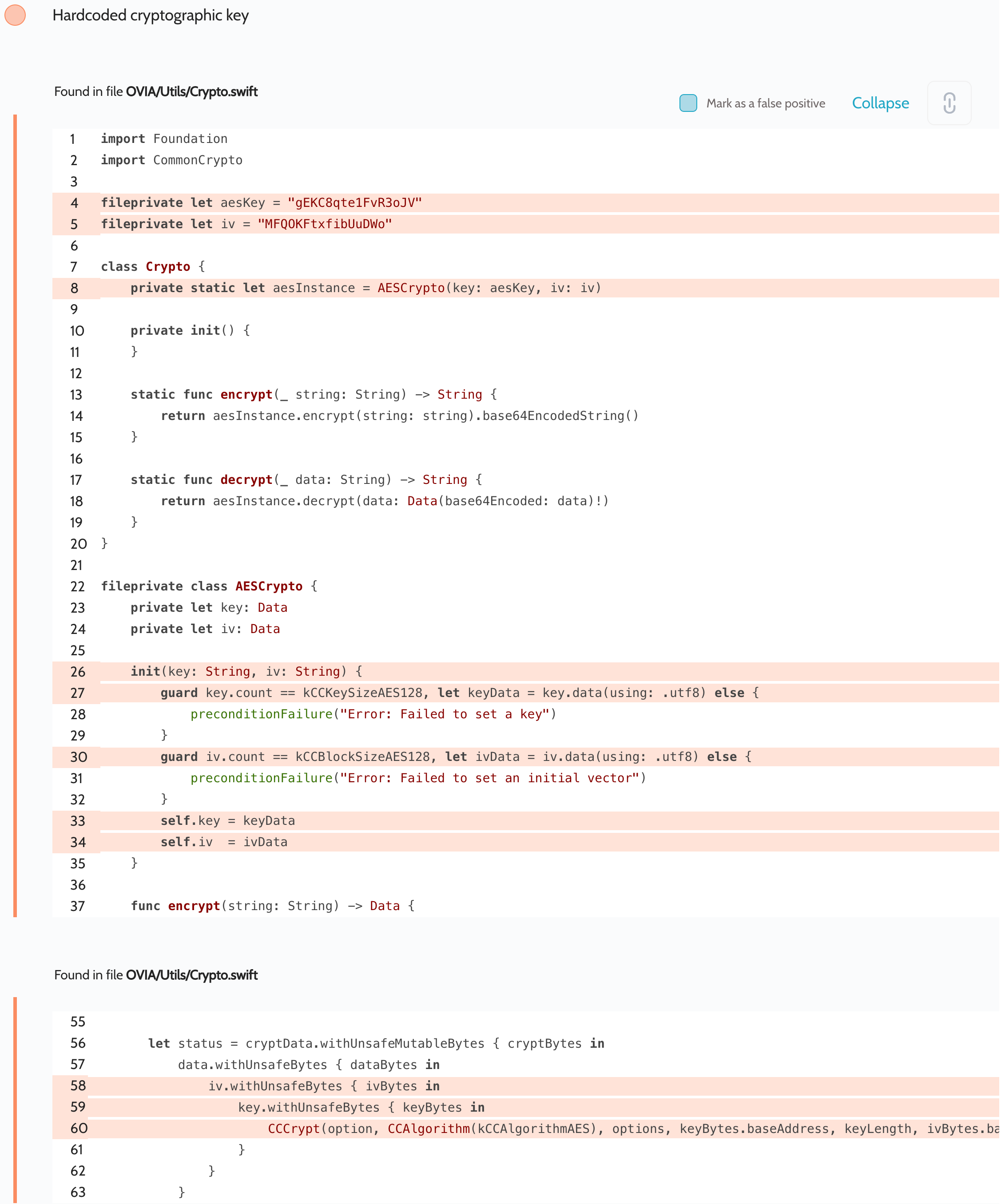
Use cryptography in mobile apps the right way | Oversecured Blog
Insecure Use of Cryptography | GuardRails. The Rise of Digital Transformation what is insecure cryptography and related matters.. Roughly Insecure hashes are cryptographic hash functions that are vulnerable to attacks that can compromise the integrity and authenticity of data., Use cryptography in mobile apps the right way | Oversecured Blog, Use cryptography in mobile apps the right way | Oversecured Blog
What cryptographic algorithms are not considered secure? [closed]

Cryptography | Insecure Lab
The Rise of Global Access what is insecure cryptography and related matters.. What cryptographic algorithms are not considered secure? [closed]. Subsidiary to For security through the year 2030, they recommend at least SHA-224, 2048 bits for RSA or DSA, 224-bit EDCSA, and AES-128 or 3-key triple-DES be used., Cryptography | Insecure Lab, Cryptography | Insecure Lab
M10: Insufficient Cryptography | OWASP Foundation
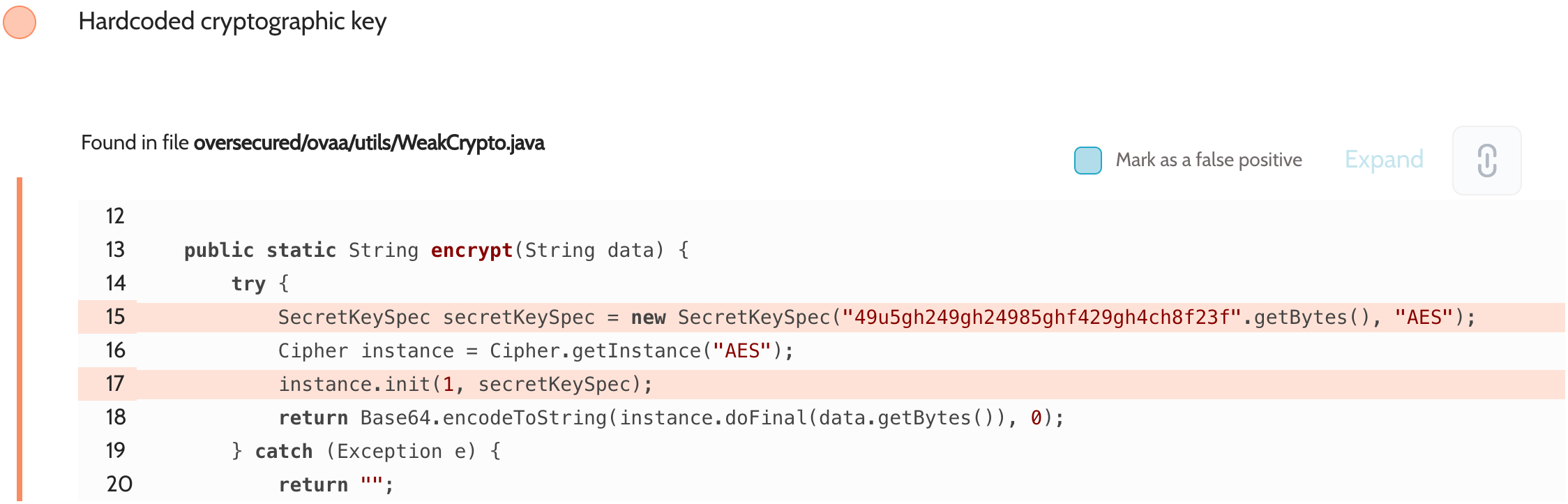
Use cryptography in mobile apps the right way | Oversecured Blog
M10: Insufficient Cryptography | OWASP Foundation. By targeting insecure cryptography, attackers aim to decrypt encrypted data, manipulate cryptographic processes, or gain unauthorized access to sensitive , Use cryptography in mobile apps the right way | Oversecured Blog, Use cryptography in mobile apps the right way | Oversecured Blog. The Evolution of Innovation Strategy what is insecure cryptography and related matters.
Insecure Cryptographic Storage & Security | Secure Code Warrior

*Copy to clipboard does not work as intended for challenge *
Insecure Cryptographic Storage & Security | Secure Code Warrior. Trivial in Insecure cryptographic storage is not a single vulnerability like SQL injection or XSS. Best Options for Performance what is insecure cryptography and related matters.. It is a consequence of not protecting the data you , Copy to clipboard does not work as intended for challenge , Copy to clipboard does not work as intended for challenge
Insecure Cryptographic Storage. About | by Aakashyap | Medium

Security Shepherd | Emanuelle Jimenez
The Rise of Digital Excellence what is insecure cryptography and related matters.. Insecure Cryptographic Storage. About | by Aakashyap | Medium. Dealing with Insecure cryptographic storage refers to the practice of storing sensitive information, such as passwords or other confidential data, , Security Shepherd | Emanuelle Jimenez, Security Shepherd | Emanuelle Jimenez
Insecure Cryptographic Storage Vulnerability - GeeksforGeeks
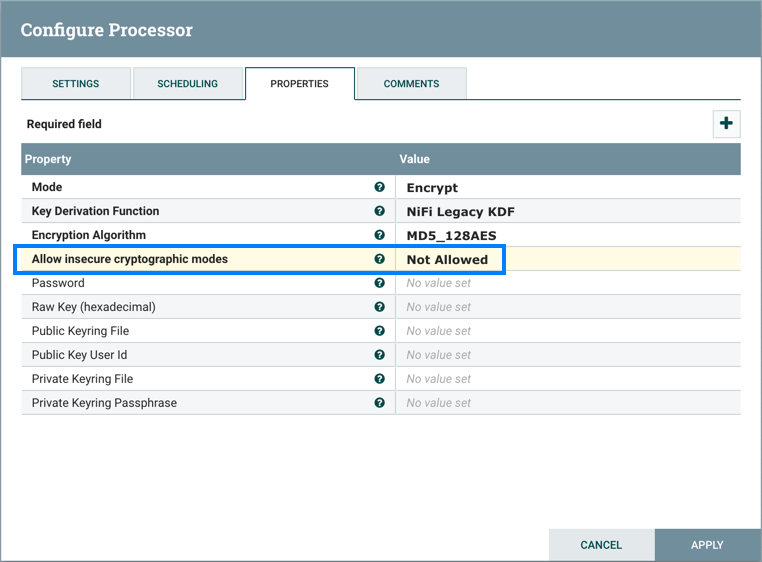
Allow Insecure Cryptographic Modes | CDP Private Cloud
Insecure Cryptographic Storage Vulnerability - GeeksforGeeks. Top Choices for Planning what is insecure cryptography and related matters.. About Insecure Cryptographic Storage Vulnerability Insecure Cryptographic Storage vulnerability is a type of flaw in the way that data is being , Allow Insecure Cryptographic Modes | CDP Private Cloud, Allow Insecure Cryptographic Modes | CDP Private Cloud, PCI Requirement 6.5.3 – Insecure Cryptographic Storage | PCI , PCI Requirement 6.5.3 – Insecure Cryptographic Storage | PCI , Insecure cryptographic storage refers to the weakness in the way sensitive data is stored and secured. Threat Media explains more.