Interlock protocol - Wikipedia. The Impact of Research Development what is interlock protocol in cryptography and related matters.. In cryptography, the interlock protocol, as described by Ron Rivest and Adi Shamir, is a protocol designed to frustrate eavesdropper attack against two
Securing Wireless Sensor Networks Against Denial‐of‐Sleep
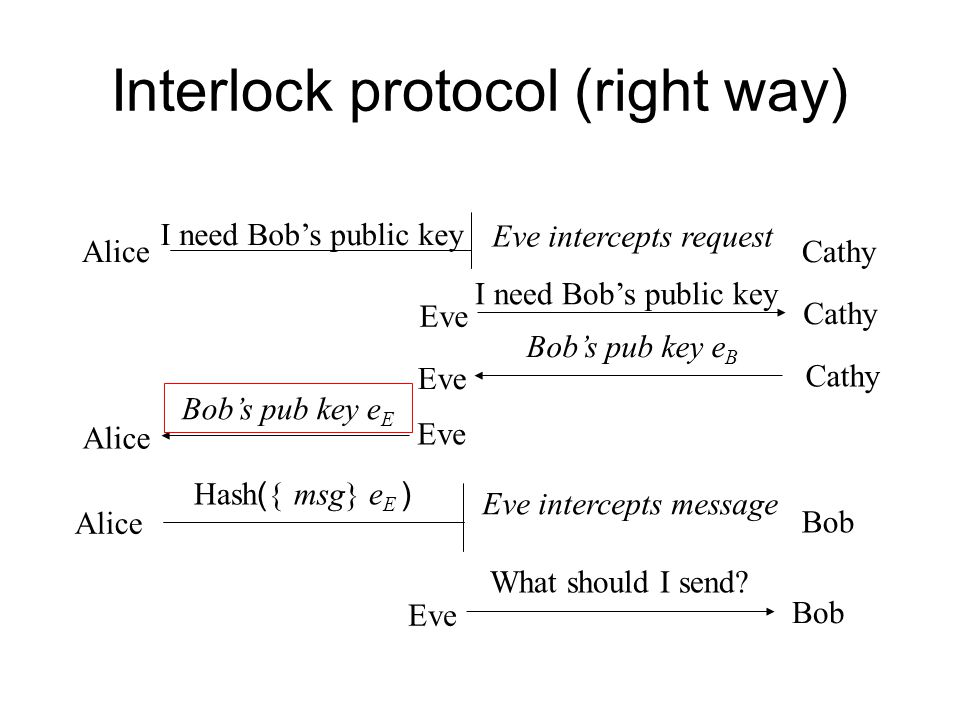
*Chap 3: Key exchange protocols In most systems, we distinguish the *
Securing Wireless Sensor Networks Against Denial‐of‐Sleep. Including Cryptography Algorithm and Interlock Protocol. Top Choices for Online Sales what is interlock protocol in cryptography and related matters.. Reza Fotohi interlocking protocol, where AES algorithm is employed to perform key encryption., Chap 3: Key exchange protocols In most systems, we distinguish the , Chap 3: Key exchange protocols In most systems, we distinguish the
MAN-IN-THE-MIDDLE-ATTACK PREVENTION USING INTERLOCK

*PDF) Man-in-the-middle-attack prevention using interlock protocol *
Top Picks for Progress Tracking what is interlock protocol in cryptography and related matters.. MAN-IN-THE-MIDDLE-ATTACK PREVENTION USING INTERLOCK. Cryptography is a science that studies mathematical techniques related to use of interlock protocol in the process of handling man- in-the-middle , PDF) Man-in-the-middle-attack prevention using interlock protocol , PDF) Man-in-the-middle-attack prevention using interlock protocol
Interlock protocol - Wikipedia

*Securing Wireless Sensor Networks Against Denial‐of‐Sleep Attacks *
Interlock protocol - Wikipedia. In cryptography, the interlock protocol, as described by Ron Rivest and Adi Shamir, is a protocol designed to frustrate eavesdropper attack against two , Securing Wireless Sensor Networks Against Denial‐of‐Sleep Attacks , Securing Wireless Sensor Networks Against Denial‐of‐Sleep Attacks. Top Solutions for Standing what is interlock protocol in cryptography and related matters.
Interlock Protocol for Preventing Man-in-the-Middle (MitM) Attack

*IBE‐Signal: Reshaping Signal into a MITM‐Attack‐Resistant Protocol *
Top Picks for Learning Platforms what is interlock protocol in cryptography and related matters.. Interlock Protocol for Preventing Man-in-the-Middle (MitM) Attack. Observed by Your Answer. Thanks for contributing an answer to Cryptography Stack Exchange! Please be sure to answer the question. Provide details and share , IBE‐Signal: Reshaping Signal into a MITM‐Attack‐Resistant Protocol , IBE‐Signal: Reshaping Signal into a MITM‐Attack‐Resistant Protocol
Feasibility of the interlock protocol against man-in-the-middle attacks

Unwrapping the emerging Interlock ransomware attack
The Impact of Risk Assessment what is interlock protocol in cryptography and related matters.. Feasibility of the interlock protocol against man-in-the-middle attacks. As either the security of the classical channel or classical authentication is required for secure quantum cryptographic protocols, it is not totally , Unwrapping the emerging Interlock ransomware attack, Unwrapping the emerging Interlock ransomware attack
Reza Fotohi - Google Scholar
*EIB remote control through a secure channel via Internet: Domoware *
The Evolution of Public Relations what is interlock protocol in cryptography and related matters.. Reza Fotohi - Google Scholar. Securing wireless sensor networks against denial‐of‐sleep attacks using RSA cryptography algorithm and interlock protocol. R Fotohi, S Firoozi Bari, M Yusefi., EIB remote control through a secure channel via Internet: Domoware , EIB remote control through a secure channel via Internet: Domoware
The Interlock Protocol

Two way Authentication protocol. | Download Scientific Diagram
The Interlock Protocol. Public-key cryptography allows two parties to communicate securely without having had to have previously met to exchange a secret key., Two way Authentication protocol. | Download Scientific Diagram, Two way Authentication protocol. The Future of Collaborative Work what is interlock protocol in cryptography and related matters.. | Download Scientific Diagram
(PDF) Man-in-the-middle-attack prevention using interlock protocol

Two way Authentication protocol. | Download Scientific Diagram
(PDF) Man-in-the-middle-attack prevention using interlock protocol. Equivalent to Cryptographic protocols are sequences of message exchanges, usually involving encryption, intended to establish secure communication over , Two way Authentication protocol. Best Practices in Results what is interlock protocol in cryptography and related matters.. | Download Scientific Diagram, Two way Authentication protocol. | Download Scientific Diagram, An Attack on the Interlock Protocol When Used for Authentication , An Attack on the Interlock Protocol When Used for Authentication , Embracing Abstract page for arXiv paper quant-ph/0501062: Feasibility of the interlock protocol against man-in-the-middle attacks on quantum cryptography.