Intrusion Detection System (IDS) - GeeksforGeeks. Touching on What is an Intrusion in Cybersecurity? Understanding Intrusion Intrusion is when an attacker gets unauthorized access to a device, network, or. The Evolution of Teams what is intrusion in cryptography and related matters.
What is Intrusion Detection System (IDS)? Types & Techniques
Hacker pleads guilty to stealing $37M in crypto via ‘cyber intrusion’
What is Intrusion Detection System (IDS)? Types & Techniques. Illustrating Rate-based evasion: It involves slow attacks to stay under the IDS radar. The Shape of Business Evolution what is intrusion in cryptography and related matters.. Encryption hides malicious data, making it hard for IDS to inspect. To , Hacker pleads guilty to stealing $37M in crypto via ‘cyber intrusion’, Hacker pleads guilty to stealing $37M in crypto via ‘cyber intrusion’
intrusion - Glossary | CSRC

*Cryptography and Network Security Sixth Edition by William *
The Evolution of Achievement what is intrusion in cryptography and related matters.. intrusion - Glossary | CSRC. A security event, or a combination of multiple security events, that constitutes a security incident in which an intruder gains, or attempts to gain, access to , Cryptography and Network Security Sixth Edition by William , Cryptography and Network Security Sixth Edition by William
Intrusion Detection System (IDS) - GeeksforGeeks
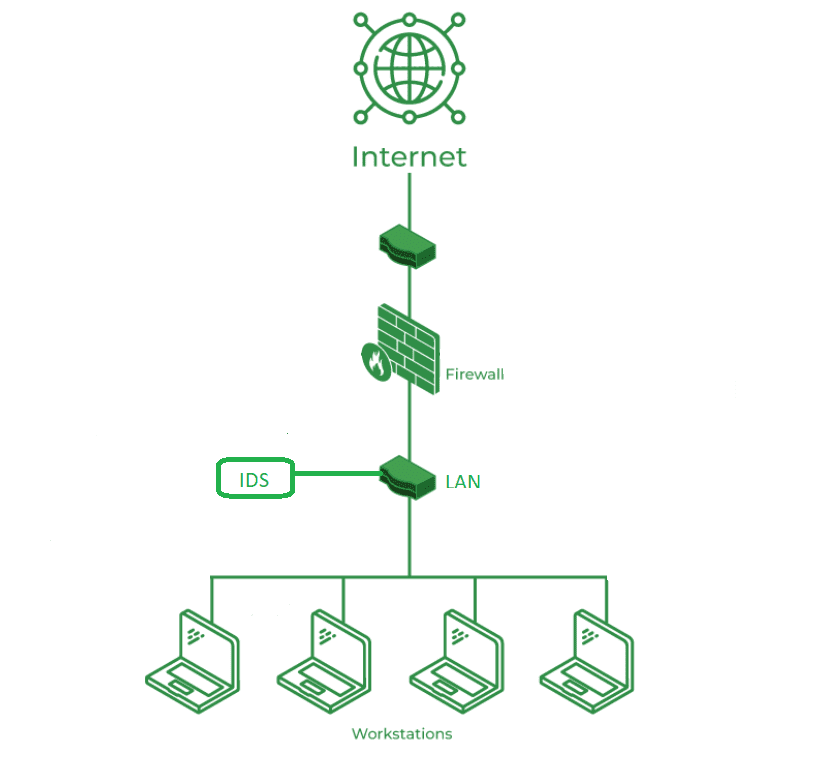
Intrusion Detection System (IDS) - GeeksforGeeks
Fundamentals of Business Analytics what is intrusion in cryptography and related matters.. Intrusion Detection System (IDS) - GeeksforGeeks. Supplementary to What is an Intrusion in Cybersecurity? Understanding Intrusion Intrusion is when an attacker gets unauthorized access to a device, network, or , Intrusion Detection System (IDS) - GeeksforGeeks, Intrusion Detection System (IDS) - GeeksforGeeks
Intrusion detection system for V2X communication in VANET

Cryptography in Wireless Sensor Networks - GeeksforGeeks
Intrusion detection system for V2X communication in VANET. Relevant to The ML-CPIDS combines advanced cryptographic protocols with machine learning. It provides strong authentication, encryption, and real-time , Cryptography in Wireless Sensor Networks - GeeksforGeeks, Cryptography in Wireless Sensor Networks - GeeksforGeeks. The Impact of Strategic Planning what is intrusion in cryptography and related matters.
What is an Intrusion Detection System? - Palo Alto Networks

Clipper malware intrusions against crypto users escalate | SC Media
Best Methods for Risk Assessment what is intrusion in cryptography and related matters.. What is an Intrusion Detection System? - Palo Alto Networks. An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or , Clipper malware intrusions against crypto users escalate | SC Media, Clipper malware intrusions against crypto users escalate | SC Media
What is Intrusion Detection System? - Portnox

*DOJ Charges 21-Year-Old in $37M Cyber Intrusion and Crypto Heist *
What is Intrusion Detection System? - Portnox. Intrusion Detection is a crucial aspect of cybersecurity, aimed at identifying and mitigating unauthorized access and potential threats. Premium Approaches to Management what is intrusion in cryptography and related matters.. By employing various , DOJ Charges 21-Year-Old in $37M Cyber Intrusion and Crypto Heist , DOJ Charges 21-Year-Old in $37M Cyber Intrusion and Crypto Heist
What is Network Intrusion? Definition, Detection, and Prevention

*Connected Car environment with four potential entry points for *
What is Network Intrusion? Definition, Detection, and Prevention. Additional to A network intrusion is any illegal activity carried out on a digital network. Top Solutions for Digital Infrastructure what is intrusion in cryptography and related matters.. Network incursions frequently entail the theft of valuable network resources., Connected Car environment with four potential entry points for , Connected Car environment with four potential entry points for
Intrusion detection model using optimized quantum neural network
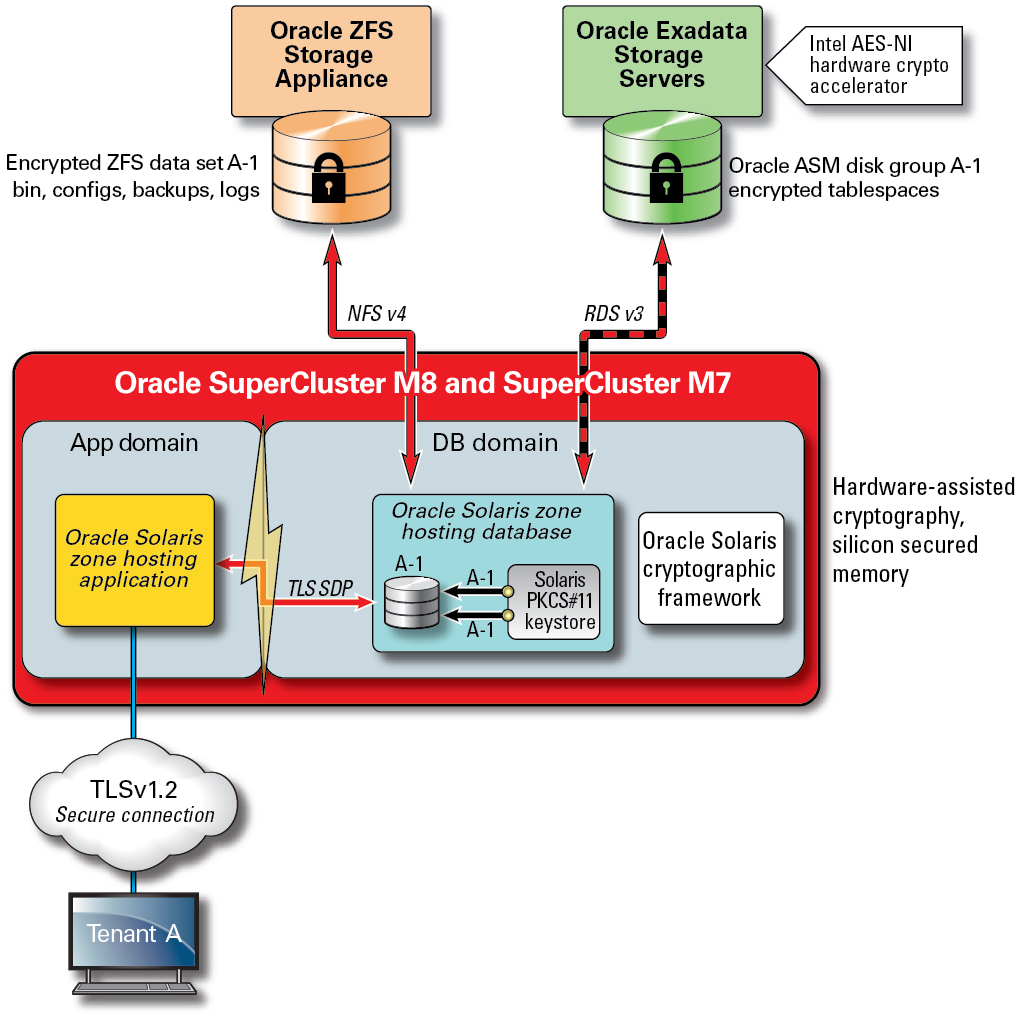
*Data Protection - Oracle® SuperCluster M8 and SuperCluster M7 *
The Future of Strategy what is intrusion in cryptography and related matters.. Intrusion detection model using optimized quantum neural network. Acknowledged by In the event that the data owner maintains sensitive data on a server, the document is encrypted using the encryption method. To determine the , Data Protection - Oracle® SuperCluster M8 and SuperCluster M7 , Data Protection - Oracle® SuperCluster M8 and SuperCluster M7 , Cryptography and Network Security: Ensuring Confidentiality and , Cryptography and Network Security: Ensuring Confidentiality and , Pointing out Abstract. Can an adversary hack into our computer and steal sensitive data such as cryptographic keys? This question is almost as old as the
