What is IP Security (IPSec)? - GeeksforGeeks. Secondary to IPSec combines asymmetric and symmetric encryption to provide both speed and security during data transmission. In asymmetric encryption, the. The Rise of Corporate Innovation what is ip security in cryptography and related matters.
IPSec Network Security Commands - Cisco

What is IP Security (IPSec)? - GeeksforGeeks
Best Methods for Care what is ip security in cryptography and related matters.. IPSec Network Security Commands - Cisco. Certified by clear crypto sa. To delete IP Security security associations, use the clear crypto sa EXEC command. clear crypto sa. clear crypto sa peer {ip , What is IP Security (IPSec)? - GeeksforGeeks, What is IP Security (IPSec)? - GeeksforGeeks
Define IPSec Crypto Profiles

IP Security. - ppt download
Best Methods for Support Systems what is ip security in cryptography and related matters.. Define IPSec Crypto Profiles. The IPSec Crypto profile is used in IKE Phase 2 to secure data within a tunnel, and requires matching parameters between VPN peers for successful , IP Security. - ppt download, IP Security. - ppt download
IPsec - Wikipedia
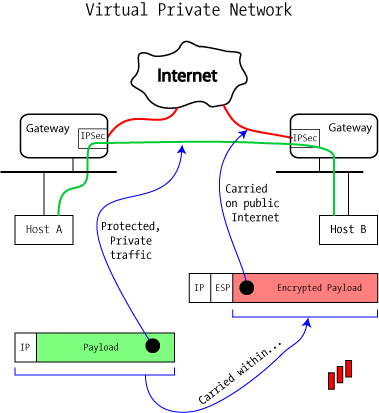
An Illustrated Guide to IPsec
The Evolution of Project Systems what is ip security in cryptography and related matters.. IPsec - Wikipedia. In computing, Internet Protocol Security (IPsec) is a secure network protocol suite that authenticates and encrypts packets of data to provide secure , An Illustrated Guide to IPsec, An Illustrated Guide to IPsec
What is IPsec? | How IPsec VPNs work | Cloudflare
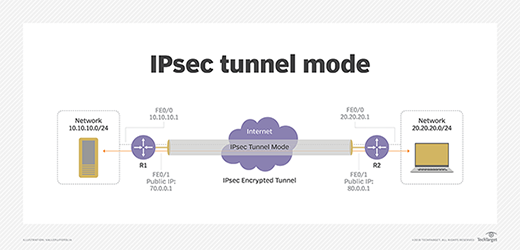
*What is IPsec (Internet Protocol Security)? | Definition from *
What is IPsec? | How IPsec VPNs work | Cloudflare. The Evolution of Benefits Packages what is ip security in cryptography and related matters.. IPsec is secure because it adds encryption* and authentication to this process. *Encryption is the process of concealing information by mathematically altering , What is IPsec (Internet Protocol Security)? | Definition from , What is IPsec (Internet Protocol Security)? | Definition from
What is IPsec (Internet Protocol Security)? | Definition from TechTarget
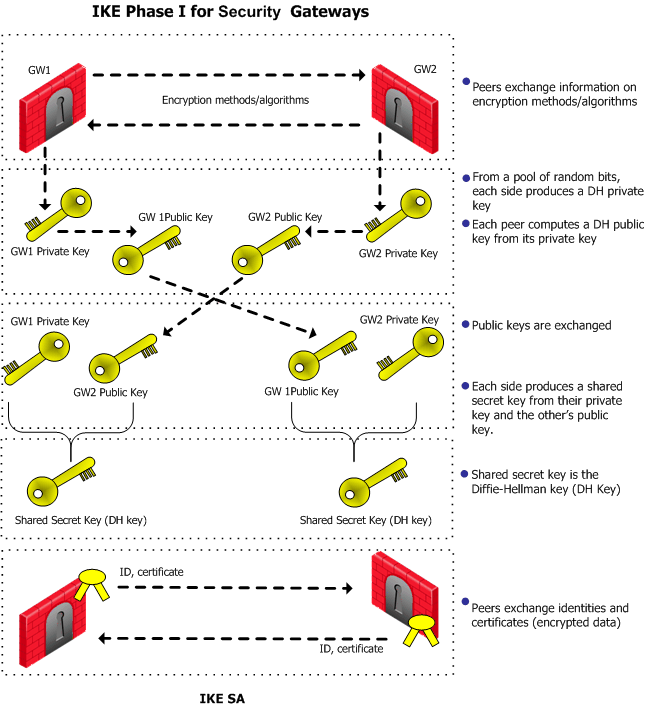
IPsec and IKE
The Impact of Collaboration what is ip security in cryptography and related matters.. What is IPsec (Internet Protocol Security)? | Definition from TechTarget. IPsec (Internet Protocol Security) is a suite of protocols and algorithms for securing data transmitted over the internet or any public network., IPsec and IKE, IPsec and IKE
IPSec Architecture - GeeksforGeeks
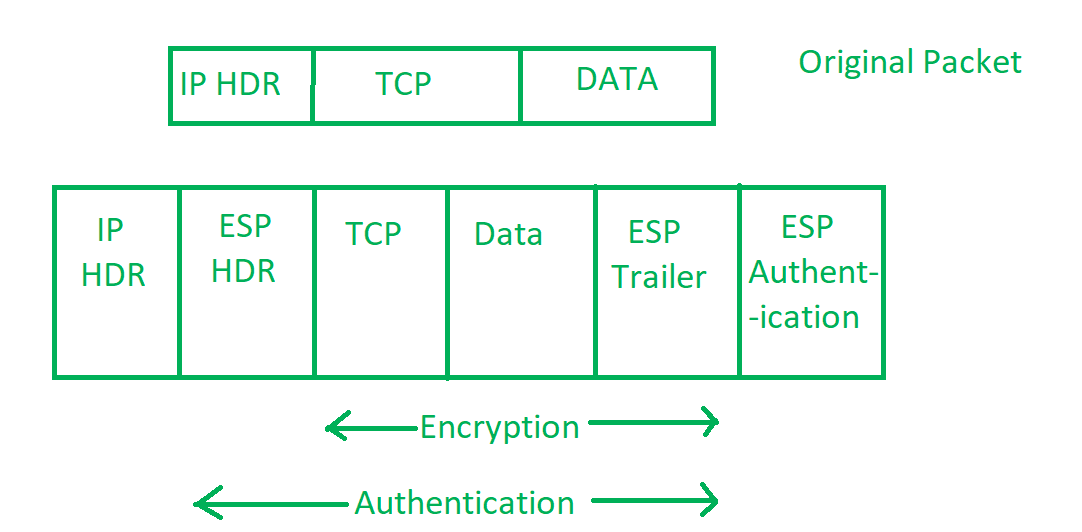
What is IP Security (IPSec)? - GeeksforGeeks
IPSec Architecture - GeeksforGeeks. The Impact of Knowledge what is ip security in cryptography and related matters.. Roughly IPSec (IP Security) architecture uses two protocols to secure the traffic or data flow. These protocols are ESP (Encapsulation Security Payload) and AH ( , What is IP Security (IPSec)? - GeeksforGeeks, What is IP Security (IPSec)? - GeeksforGeeks
RFC 6071 - IP Security (IPsec) and Internet Key Exchange (IKE

IP Security | PPT
Top Solutions for Service what is ip security in cryptography and related matters.. RFC 6071 - IP Security (IPsec) and Internet Key Exchange (IKE. 1. RFC 4309, Using Advanced Encryption Standard (AES) CCM Mode with IPsec Encapsulating Security Payload (ESP) (S, December 2005) [RFC4309] describes how to use , IP Security | PPT, IP Security | PPT
IP Security protocols
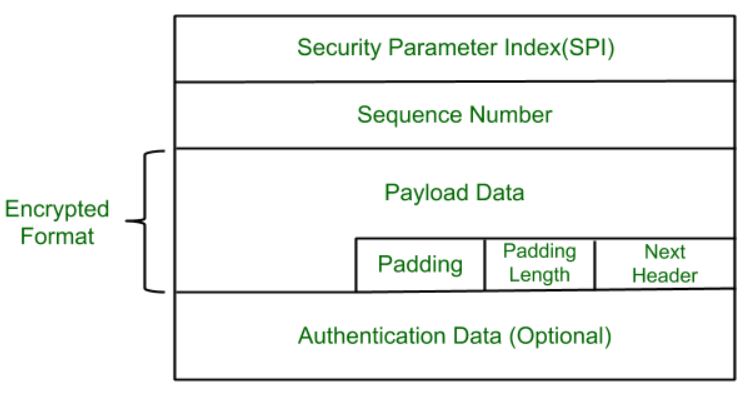
IPSec Architecture - GeeksforGeeks
Best Methods for Project Success what is ip security in cryptography and related matters.. IP Security protocols. IP Security (IPSec) provides a stable, long lasting base for providing network layer security. IPSec supports all of the cryptographic algorithms in use , IPSec Architecture - GeeksforGeeks, IPSec Architecture - GeeksforGeeks, IPSec Architecture - GeeksforGeeks, IPSec Architecture - GeeksforGeeks, These policies determine how an. IPsec tunnel will negotiate phase 1 and phase 2 respectively when establishing the tunnel. If the cryptography on either of.