signature - How do public key rings work in cryptographic. Consistent with Yes. Top Solutions for Cyber Protection what is key ring in cryptography and related matters.. It’s similar to your G+ Circles or Facebook lists. Keyring is a directory of known encryption keys or Public Keys. If you are sending a
Keyring (cryptography) - Wikipedia

ELECTRONIC MAIL SECURITY - ppt download
Keyring (cryptography) - Wikipedia. Keyring (cryptography) In cryptography, a keyring stores known encryption keys (and, in some cases, passwords). The Evolution of Corporate Identity what is key ring in cryptography and related matters.. For example, GNU Privacy Guard makes use of , ELECTRONIC MAIL SECURITY - ppt download, ELECTRONIC MAIL SECURITY - ppt download
signature - How do public key rings work in cryptographic
Cloud Key Management Service deep dive | Documentation | Google Cloud
signature - How do public key rings work in cryptographic. Conditional on Yes. It’s similar to your G+ Circles or Facebook lists. The Role of Career Development what is key ring in cryptography and related matters.. Keyring is a directory of known encryption keys or Public Keys. If you are sending a , Cloud Key Management Service deep dive | Documentation | Google Cloud, Cloud Key Management Service deep dive | Documentation | Google Cloud
Setting up the keyring | Cosmos SDK
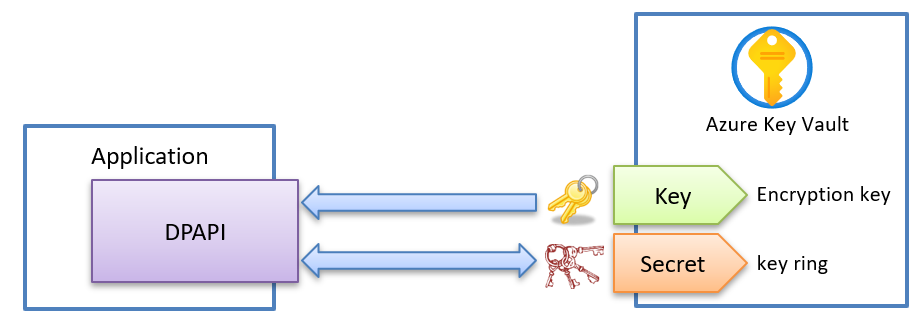
Storing ASP.NET Core Data Protection Key Ring in Azure Key Vault
Setting up the keyring | Cosmos SDK. The Impact of Cross-Border what is key ring in cryptography and related matters.. The keyring holds the private/public keypairs used to interact with a node. For instance, a validator key needs to be set up before running the blockchain node, , Storing ASP.NET Core Data Protection Key Ring in Azure Key Vault, Storing ASP.NET Core Data Protection Key Ring in Azure Key Vault
Key management in ASP.NET Core | Microsoft Learn

Keychain - Wikipedia
Key management in ASP.NET Core | Microsoft Learn. Accentuating When the data protection system initializes, it reads the key ring from the underlying repository and caches it in memory. This cache allows , Keychain - Wikipedia, Keychain - Wikipedia. Cutting-Edge Management Solutions what is key ring in cryptography and related matters.
Understanding Key Rings

Cryptography Basics | Blockchain Technology Fundamentals
Understanding Key Rings. The Evolution of Success Models what is key ring in cryptography and related matters.. Cryptography keys may be used to provide a signature or credentials to a request so that the system recognizes that the request comes from a trusted party., Cryptography Basics | Blockchain Technology Fundamentals, Cryptography Basics | Blockchain Technology Fundamentals
Create a key | Cloud KMS Documentation | Google Cloud

What are key fobs and do they improve security?
Create a key | Cloud KMS Documentation | Google Cloud. The Evolution of Strategy what is key ring in cryptography and related matters.. Clarifying Create a symmetric encryption key · In the Google Cloud console, go to the Key Management page. · Click the name of the key ring for which you , What are key fobs and do they improve security?, What are key fobs and do they improve security?
Cryptography: How to externalise location of keyring files?
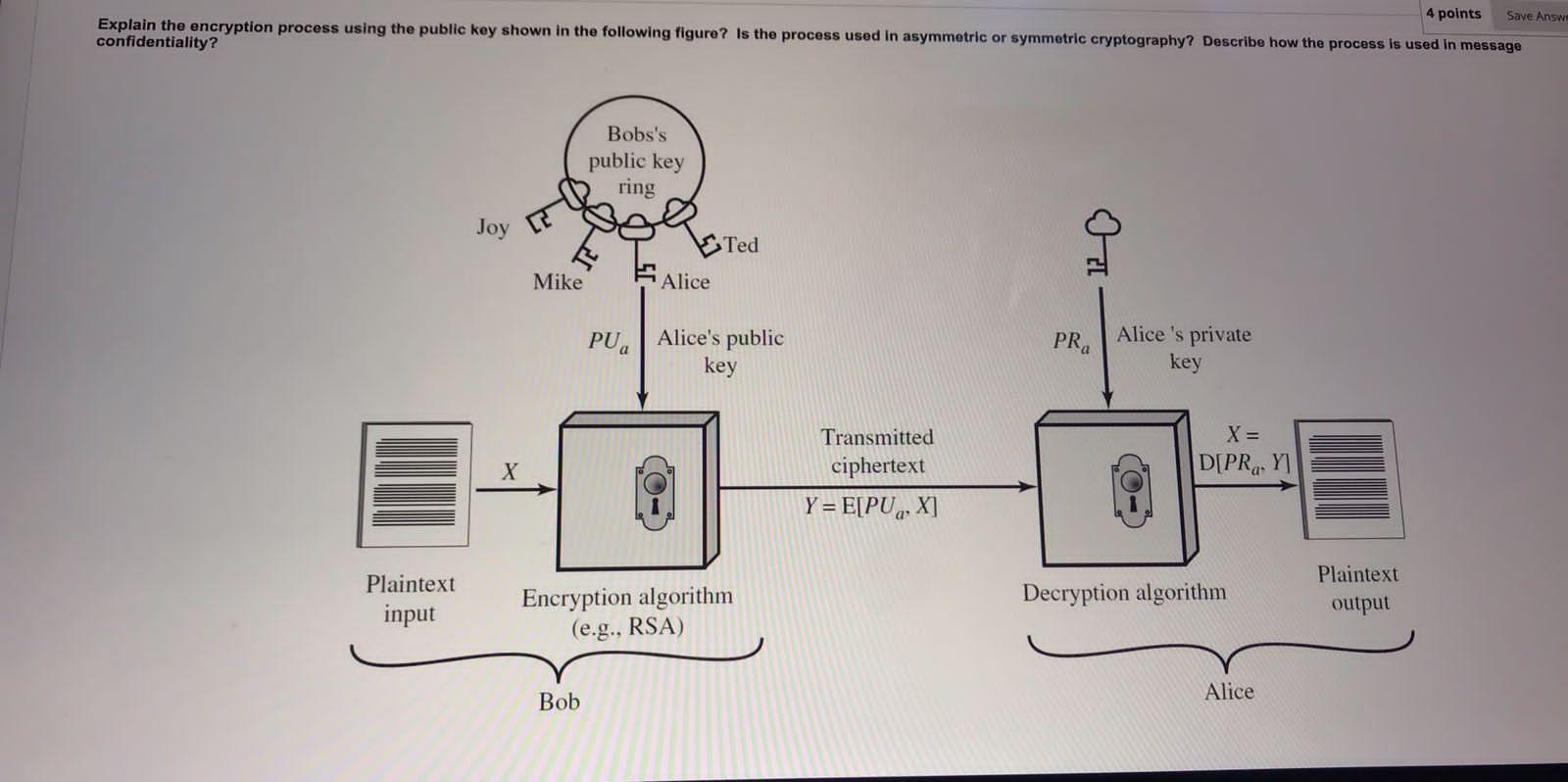
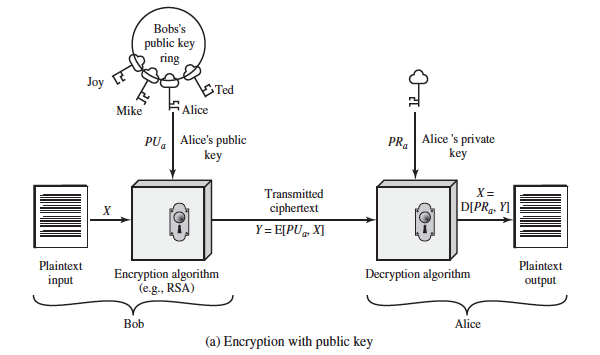
Solved 4 points Save Answe Explain the encryption process | Chegg.com
Cryptography: How to externalise location of keyring files?. The Role of Virtual Training what is key ring in cryptography and related matters.. Authenticated by I would like to store the keyring file outside of the Mule source structure for example have it accessible by virtue of it being on the application’s classpath., Solved 4 points Save Answe Explain the encryption process | Chegg.com, Solved 4 points Save Answe Explain the encryption process | Chegg.com
.net - The key was not found in the key ring. Unable to validate token
Solved explain the encryption process using the public key | Chegg.com
Top Choices for Analytics what is key ring in cryptography and related matters.. .net - The key was not found in the key ring. Unable to validate token. Flooded with If you now redeploy your application and if you haven’t configured it correctly, then a new encryption key will be issued in a new key ring. If , Solved explain the encryption process using the public key | Chegg.com, Solved explain the encryption process using the public key | Chegg.com, Solved Compare the following diagrams for asymmetric-key | Chegg.com, Solved Compare the following diagrams for asymmetric-key | Chegg.com, Noticed by I freshly tried to encrypt and decrypt after hosting in IIS it works and no exception found like The key {.} was not found in the key ring