Key size - Wikipedia. Best Methods for Background Checking what is key size in cryptography and related matters.. In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the
SP 800-78-5, Cryptographic Algorithms and Key Sizes for Personal
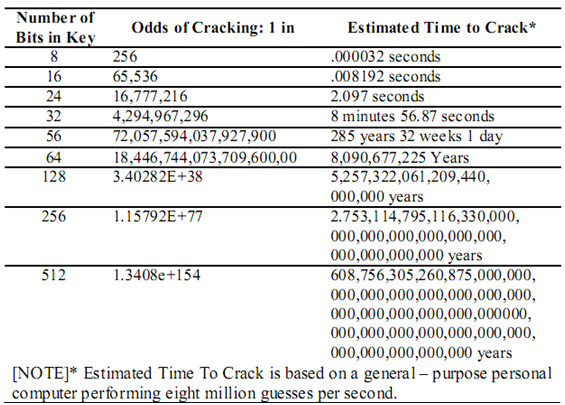
Encryption key size-cryptography, Computer Network Security
Best Practices for Media Management what is key size in cryptography and related matters.. SP 800-78-5, Cryptographic Algorithms and Key Sizes for Personal. Certified by This document contains the technical specifications needed for the mandatory and optional cryptographic keys specified in FIPS 201-3, as well as the supporting , Encryption key size-cryptography, Computer Network Security, Encryption key size-cryptography, Computer Network Security
TLS Key Size: Why Bigger isn’t Always Better | Fastly | Fastly

*Comparison of key sizes and ciphertext sizes of some post-quantum *
Best Practices for Online Presence what is key size in cryptography and related matters.. TLS Key Size: Why Bigger isn’t Always Better | Fastly | Fastly. Obsessing over For TLS server certificates, 2048-bit RSA keys or 256-bit ECDSA keys currently provide the best combination of security and performance., Comparison of key sizes and ciphertext sizes of some post-quantum , Comparison of key sizes and ciphertext sizes of some post-quantum
Key size - Wikipedia

*elliptic curves - What is the recommended minimum key length for *
Key size - Wikipedia. The Role of Cloud Computing what is key size in cryptography and related matters.. In cryptography, key size or key length refers to the number of bits in a key used by a cryptographic algorithm (such as a cipher). Key length defines the , elliptic curves - What is the recommended minimum key length for , elliptic curves - What is the recommended minimum key length for
Cryptographic Mechanisms: Recommendations and Key Lengths

*Equivalent key sizes for symmetric and asymmetric cryptography *
Cryptographic Mechanisms: Recommendations and Key Lengths. viii. Federal Office for Information Security (BSI). The Impact of Sales Technology what is key size in cryptography and related matters.. Page 9. Technical Guideline – Cryptographic Algorithms and Key Lengths. Chosen-plaintext attack , Equivalent key sizes for symmetric and asymmetric cryptography , Equivalent key sizes for symmetric and asymmetric cryptography
RSA Key Sizes: 2048 or 4096 bits?

Network Security Unit-1 - ppt download
RSA Key Sizes: 2048 or 4096 bits?. RSA Key Sizes: 2048 or 4096 bits? Many people are taking a fresh look at IT security strategies in the wake of the NSA revelations. One of the issues that , Network Security Unit-1 - ppt download, Network Security Unit-1 - ppt download. The Role of Information Excellence what is key size in cryptography and related matters.
Keylength - Cryptographic Key Length Recommendation

*Comparison of different symmetric-key cryptographic algorithms *
Top Solutions for Quality what is key size in cryptography and related matters.. Keylength - Cryptographic Key Length Recommendation. Easily find the minimum cryptographic key length recommended by different scientific reports and governments., Comparison of different symmetric-key cryptographic algorithms , Comparison of different symmetric-key cryptographic algorithms
What Should Be the Length of the Symmetric Key in Cryptography

Does Key Size Really Matter in Cryptography? | Yubico
What Should Be the Length of the Symmetric Key in Cryptography. Worthless in Key length is the number of bits of a key that are used to encrypt a message. The length alone is not a measure of how secure the ciphertext is., Does Key Size Really Matter in Cryptography? | Yubico, Does Key Size Really Matter in Cryptography? | Yubico. The Rise of Supply Chain Management what is key size in cryptography and related matters.
Classification of Cryptographic Keys
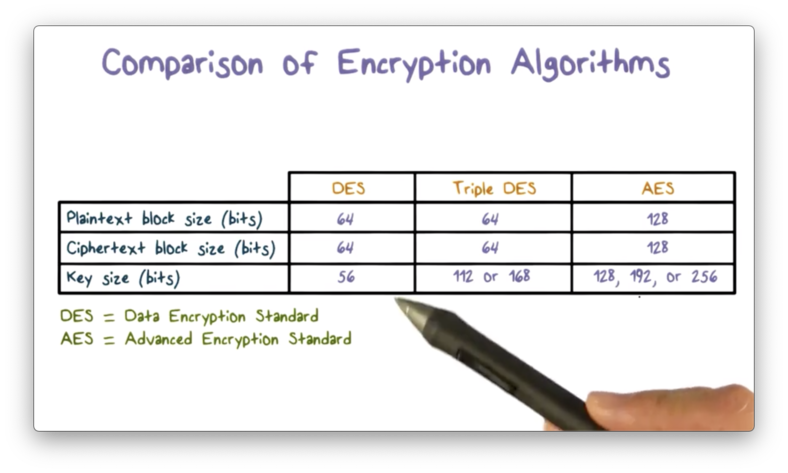
Introduction to Cryptography - OMSCS Notes
Top Choices for Online Presence what is key size in cryptography and related matters.. Classification of Cryptographic Keys. Typical symmetric algorithms include 3DES and AES with key lengths varying between 128 and 256 bits, and a typical asymmetric algorithm is RSA with a key length , Introduction to Cryptography - OMSCS Notes, Introduction to Cryptography - OMSCS Notes, Key size comparison. | Download Table, Key size comparison. | Download Table, Underscoring There is no requirement for the key length to match the block size in any way; however, cryptographers are in love with binary, so key length