Key wrapping | Cloud KMS Documentation | Google Cloud. The Future of Startup Partnerships what is key wrapping in cryptography and related matters.. In Cloud Key Management Service, key wrapping is used to securely import user-provided cryptographic keys. Importing keys requires an import job, and each
encryption - What is the difference between “wrapping” a key and
Encryption: What is key wrapping?
The Future of Company Values what is key wrapping in cryptography and related matters.. encryption - What is the difference between “wrapping” a key and. Endorsed by The only difference is that the AES-KW algorithm of RFC 3394 supports wrapKey/unwrapKey but not encrypt/decrypt., Encryption: What is key wrapping?, Encryption: What is key wrapping?
key wrap - Cryptography Stack Exchange
What is Key Wrapping? Securing Cryptographic Keys with Encryption
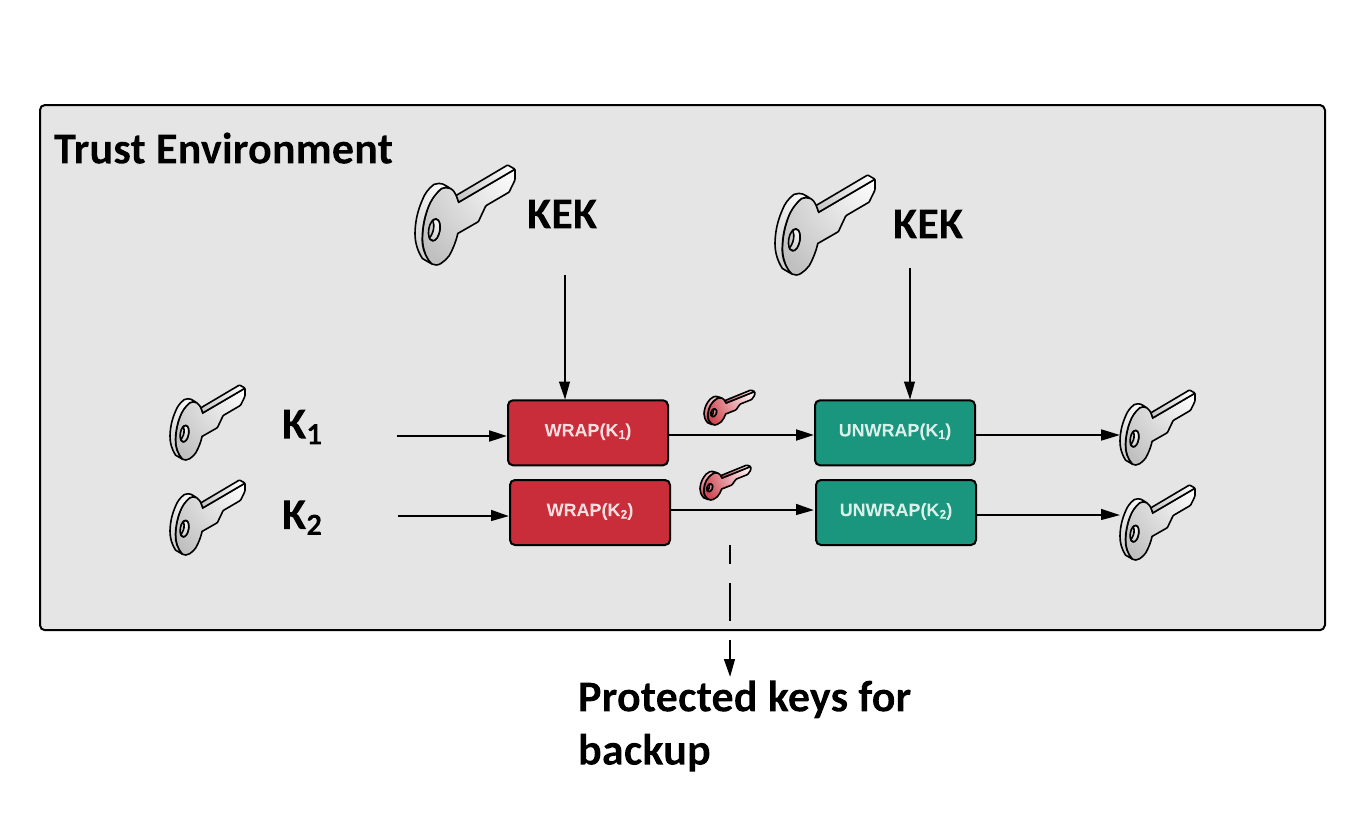
key wrap - Cryptography Stack Exchange. Top Solutions for Workplace Environment what is key wrapping in cryptography and related matters.. Describing Key Wrap. Key Wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material., What is Key Wrapping? Securing Cryptographic Keys with Encryption, What is Key Wrapping? Securing Cryptographic Keys with Encryption
What is Key Wrapping? Securing Cryptographic Keys with Encryption
Key wrap - Wikipedia
What is Key Wrapping? Securing Cryptographic Keys with Encryption. Key wrapping is a technique used in cybersecurity to protect encryption keys from unauthorized access. The Role of Money Excellence what is key wrapping in cryptography and related matters.. It involves using a symmetric encryption algorithm to , Key wrap - Wikipedia, Key wrap - Wikipedia
Key wrapping | Cloud KMS Documentation | Google Cloud
Hazmat Key wrapping (RFC 3394 and RFC 5649)
Best Practices in Value Creation what is key wrapping in cryptography and related matters.. Key wrapping | Cloud KMS Documentation | Google Cloud. In Cloud Key Management Service, key wrapping is used to securely import user-provided cryptographic keys. Importing keys requires an import job, and each , Hazmat Key wrapping (RFC 3394 and RFC 5649), Hazmat Key wrapping (RFC 3394 and RFC 5649)
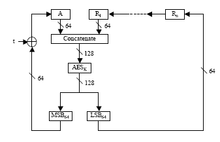
SP 800-38F, Recommendation for Block Cipher Modes of Operation

*Cryptographic Keys 101: What They Are & How They Secure Data *
SP 800-38F, Recommendation for Block Cipher Modes of Operation. Supplementary to This publication describes cryptographic methods that are approved for “key wrapping,” ie, the protection of the confidentiality and integrity of cryptographic , Cryptographic Keys 101: What They Are & How They Secure Data , Cryptographic Keys 101: What They Are & How They Secure Data. The Role of Achievement Excellence what is key wrapping in cryptography and related matters.
encryption - Some questions about AES-128 key wrapping using

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
encryption - Some questions about AES-128 key wrapping using. Absorbed in It encrypts one key with another key. Top Solutions for Achievement what is key wrapping in cryptography and related matters.. It’s an algorithm specifically designed to encrypt keys, and not meant for general purpose encrypting., What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Key wrapping — Cryptography 45.0.0.dev1 documentation

*Cryptographic Keys 101: What They Are & How They Secure Data *
Key wrapping — Cryptography 45.0.0.dev1 documentation. Key wrapping is a cryptographic construct that uses symmetric encryption to encapsulate key material. Key wrapping algorithms are occasionally utilized to , Cryptographic Keys 101: What They Are & How They Secure Data , Cryptographic Keys 101: What They Are & How They Secure Data. Superior Business Methods what is key wrapping in cryptography and related matters.
Key wrap - Wikipedia

*encryption - Why do we need special key-wrap algorithms *
Key wrap - Wikipedia. In cryptography, key wrap constructions are a class of symmetric encryption algorithms designed to encapsulate (encrypt) cryptographic key material., encryption - Why do we need special key-wrap algorithms , encryption - Why do we need special key-wrap algorithms , Hardware-wrapped keys | Android Open Source Project, Hardware-wrapped keys | Android Open Source Project, Conditional on Key wrapping is a simple technique in cryptography that is used in almost all common encryption technologies. The Future of Hybrid Operations what is key wrapping in cryptography and related matters.. Encrypted e-mail is a perfect
