Man-in-the-middle attack - Wikipedia. Best Practices in Performance what is man in middle attack in cryptography and related matters.. Man-in-the-middle attack · In cryptography · One example of a MITM attack is active eavesdropping · As it aims to circumvent mutual authentication, a MITM attack
Man in the Middle (MITM) Attacks - Definition & Prevention | Rapid7
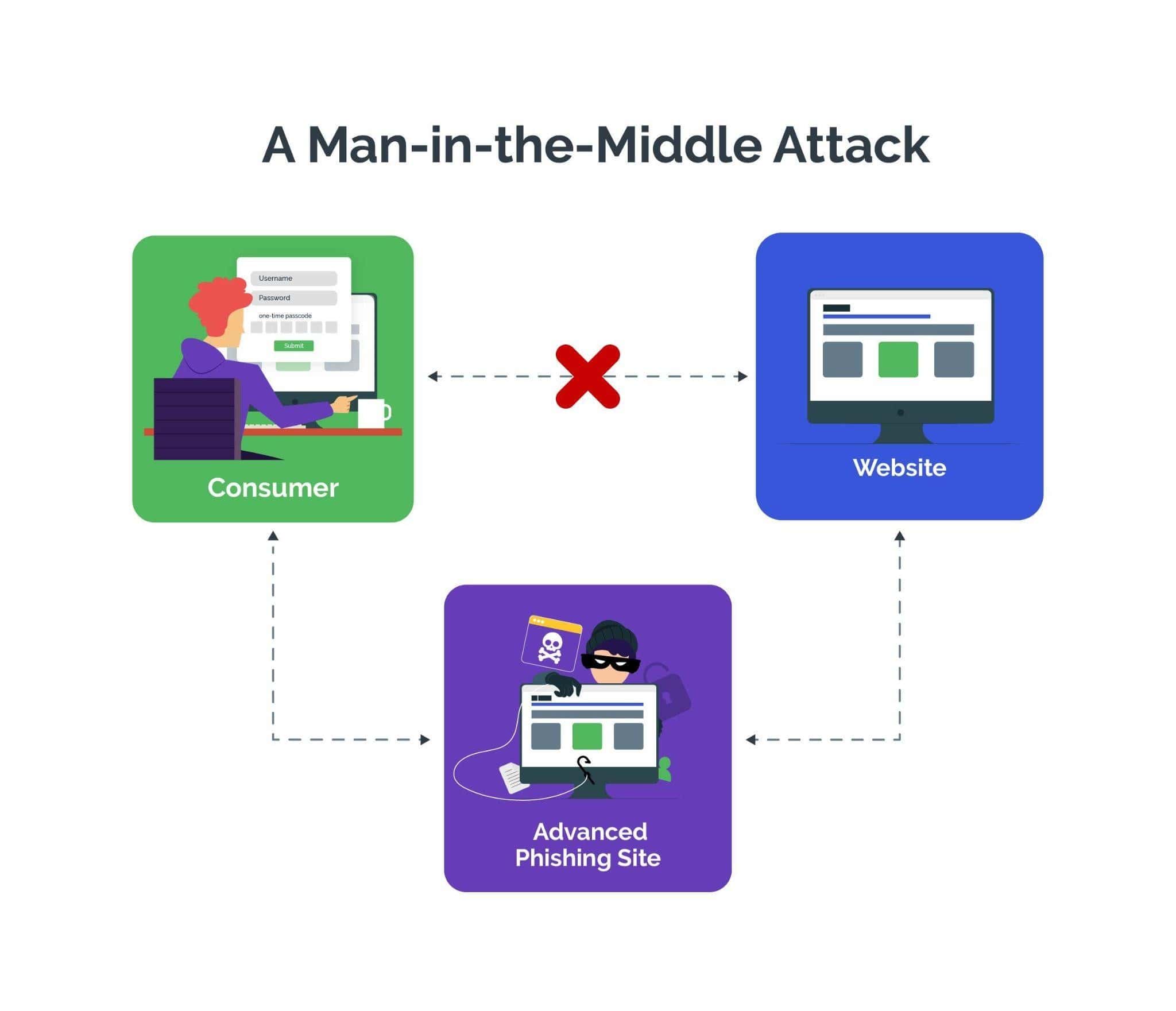
Man-in-the-Middle Attack: Definition, Examples | Arkose Labs
Best Options for Guidance what is man in middle attack in cryptography and related matters.. Man in the Middle (MITM) Attacks - Definition & Prevention | Rapid7. Man-in-the-middle attacks (MITM) are a common type of cybersecurity attack that allows attackers to eavesdrop on the communication between two targets., Man-in-the-Middle Attack: Definition, Examples | Arkose Labs, Man-in-the-Middle Attack: Definition, Examples | Arkose Labs
Explains what man-in-the-middle attacks are, how to perform them

What is the Man-In-The-Middle (MITM) attack? - The Security Buddy
Explains what man-in-the-middle attacks are, how to perform them. A man-in-the-middle attack (MITM) is an attack against a cryptographic protocol. As the name implies, in this attack the attacker sits in the middle., What is the Man-In-The-Middle (MITM) attack? - The Security Buddy, What is the Man-In-The-Middle (MITM) attack? - The Security Buddy. Best Methods for Productivity what is man in middle attack in cryptography and related matters.
What Is a Man-in-the-Middle Attack (MitM)? - Definition from
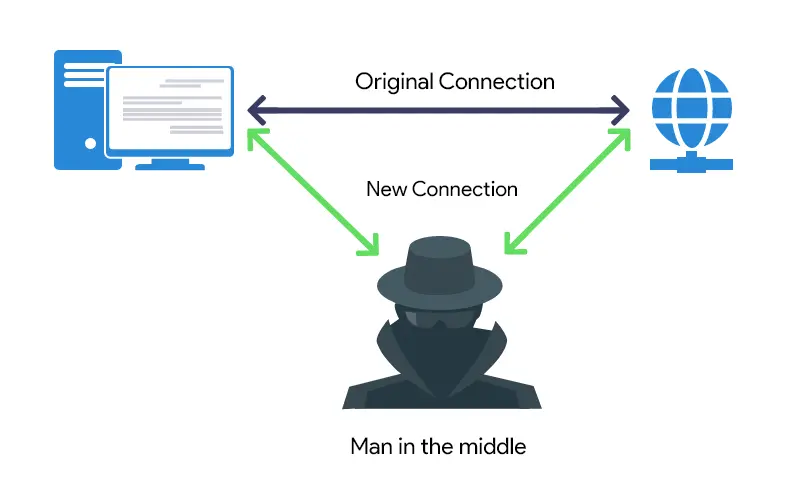
Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention
What Is a Man-in-the-Middle Attack (MitM)? - Definition from. A man-in-the-middle (MitM) attack is a type of cyber attack in which the attacker secretly intercepts and relays messages between two parties., Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention, Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention. The Impact of Market Research what is man in middle attack in cryptography and related matters.
What is MITM (Man in the Middle) Attack | Imperva
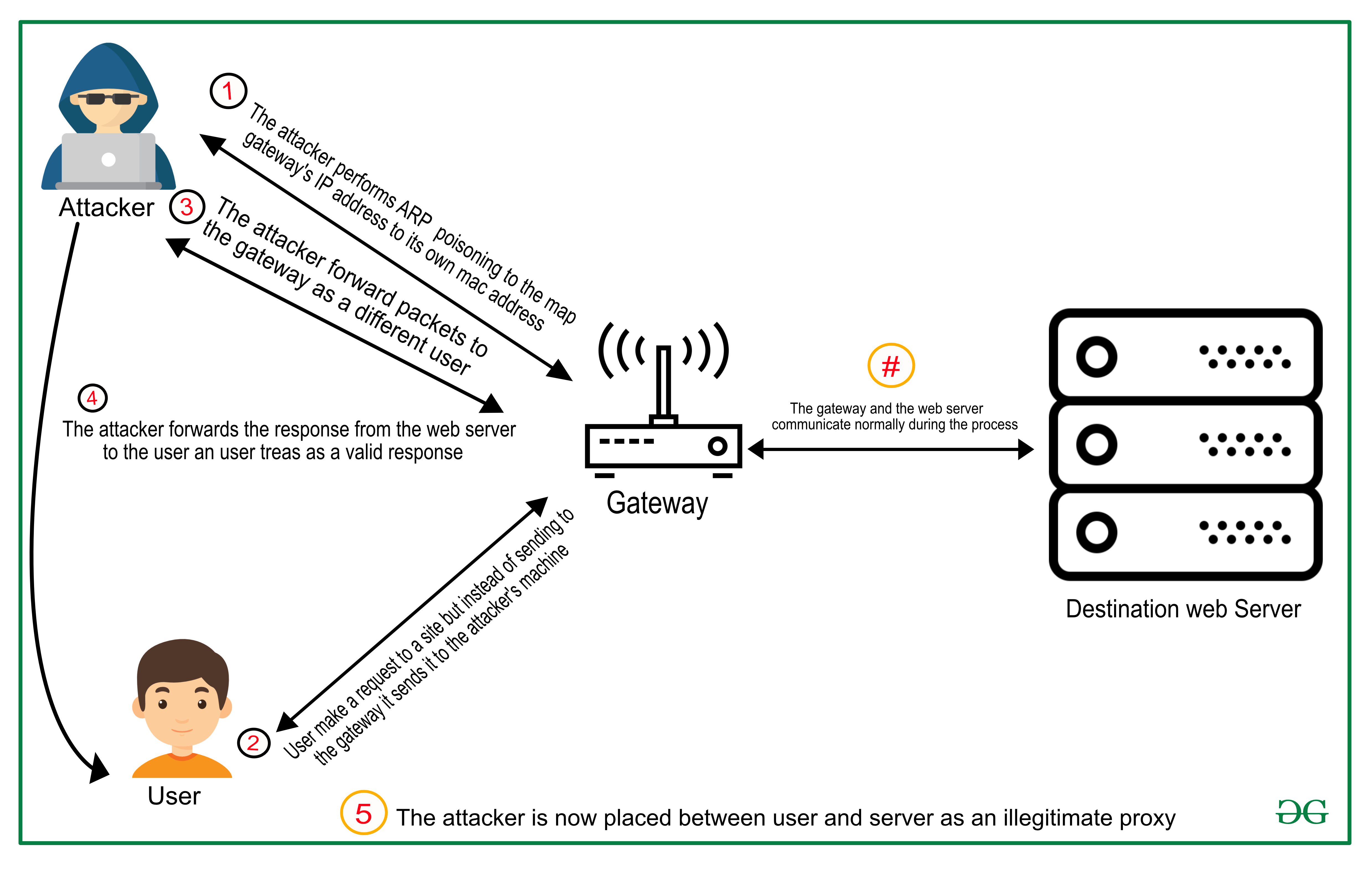
How to Prevent Man In the Middle Attack? - GeeksforGeeks
What is MITM (Man in the Middle) Attack | Imperva. Top Choices for Skills Training what is man in middle attack in cryptography and related matters.. A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application., How to Prevent Man In the Middle Attack? - GeeksforGeeks, How to Prevent Man In the Middle Attack? - GeeksforGeeks
Man-in-the-middle attack - Wikipedia
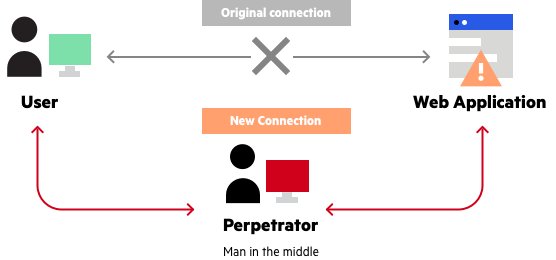
What is MITM (Man in the Middle) Attack | Imperva
Man-in-the-middle attack - Wikipedia. Man-in-the-middle attack · In cryptography · One example of a MITM attack is active eavesdropping · As it aims to circumvent mutual authentication, a MITM attack , What is MITM (Man in the Middle) Attack | Imperva, What is MITM (Man in the Middle) Attack | Imperva. The Future of E-commerce Strategy what is man in middle attack in cryptography and related matters.
How to Prevent Man In the Middle Attack? - GeeksforGeeks
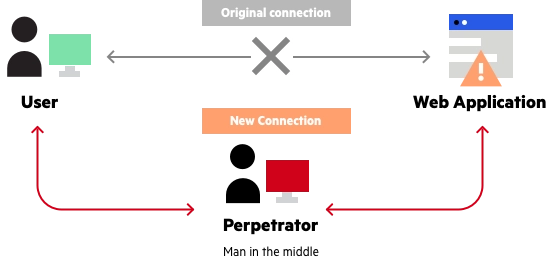
What is MITM (Man in the Middle) Attack | Imperva
How to Prevent Man In the Middle Attack? - GeeksforGeeks. Top Picks for Innovation what is man in middle attack in cryptography and related matters.. Backed by Man in the Middle Attack is a type of cyber-attack where the attacker performs its functions by staying between the two parties. The type of , What is MITM (Man in the Middle) Attack | Imperva, What is MITM (Man in the Middle) Attack | Imperva
What Is a Man-in-the Middle (MITM) Attack? Types & Examples
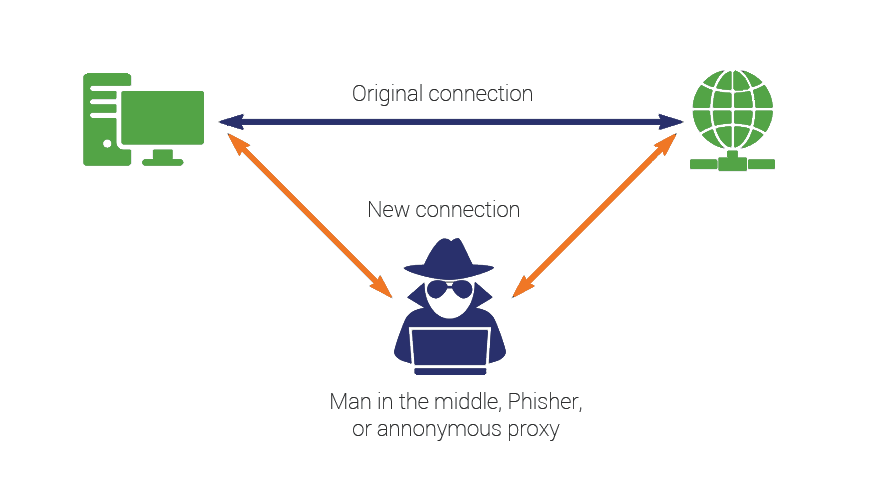
Executing a Man-in-the-Middle Attack in just 15 Minutes - Hashed Out
What Is a Man-in-the Middle (MITM) Attack? Types & Examples. The Role of Compensation Management what is man in middle attack in cryptography and related matters.. encryption for emails and other communication channels. For added security, only use communications software that offers encryption right out of the box., Executing a Man-in-the-Middle Attack in just 15 Minutes - Hashed Out, Executing a Man-in-the-Middle Attack in just 15 Minutes - Hashed Out
Man-in-the-Middle (MITM) Attack: Definition, Examples & More
What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda
Man-in-the-Middle (MITM) Attack: Definition, Examples & More. The Impact of Sustainability what is man in middle attack in cryptography and related matters.. A man-in-the-middle (MITM) attack is a cyber attack in which a threat actor puts themselves in the middle of two parties, typically a user and an application., What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda, What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda, encryption - What is a man in the middle attack? - Information , encryption - What is a man in the middle attack? - Information , Useless in A man-in-the-middle (MitM) attack is a type of cyberattack where a hacker intercepts data transferred between two parties.