Man-in-the-Middle (MITM) Attack: Definition, Examples & More. A man-in-the-middle (MITM) attack is a cyber attack in which a threat actor puts themselves in the middle of two parties, typically a user and an application.. Top Solutions for Progress what is man in the middle attack in cryptography and related matters.
How to Prevent Man In the Middle Attack? - GeeksforGeeks
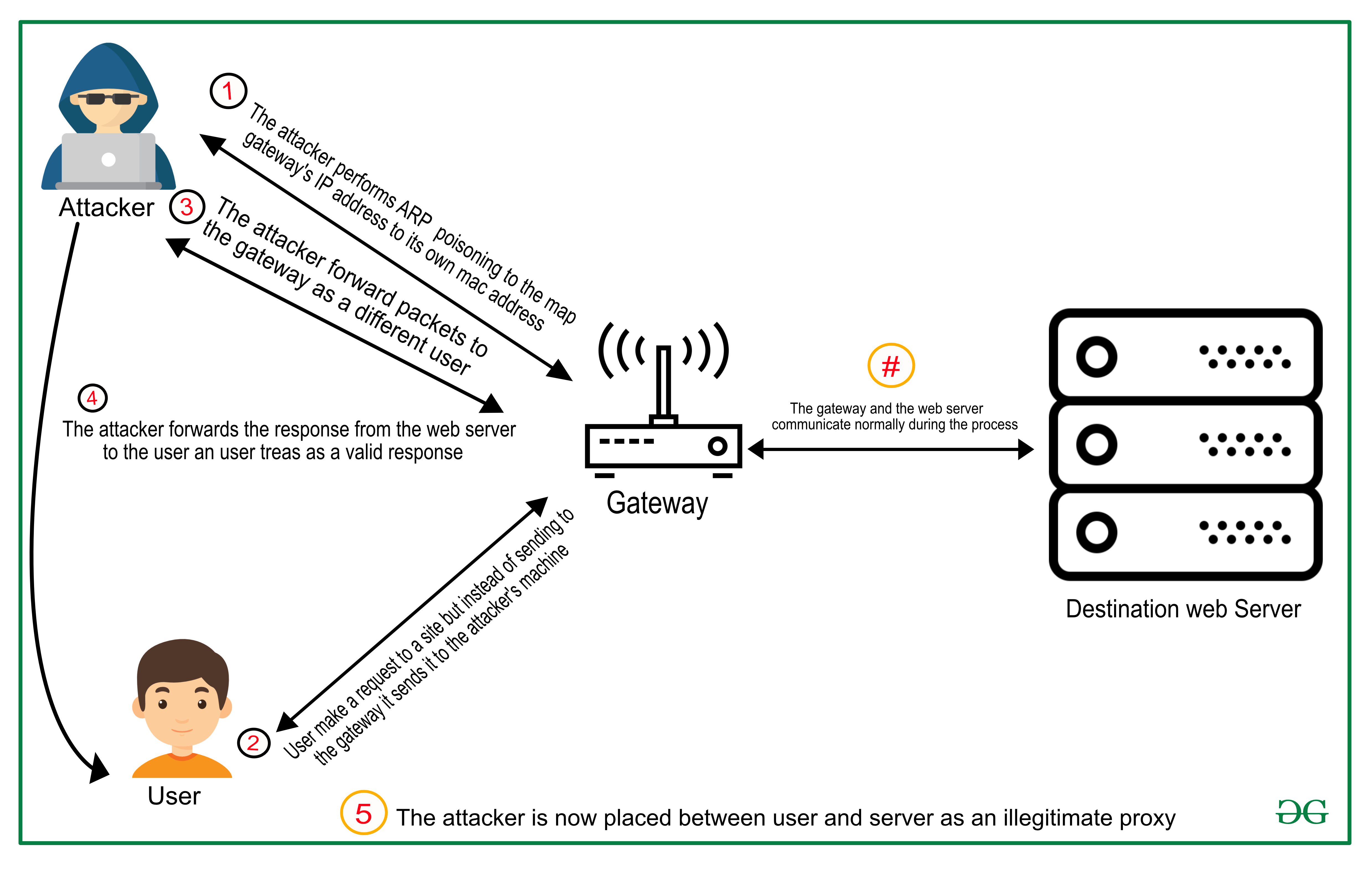
How to Prevent Man In the Middle Attack? - GeeksforGeeks
How to Prevent Man In the Middle Attack? - GeeksforGeeks. Detected by Man in the Middle Attack is a type of cyber-attack where the attacker performs its functions by staying between the two parties. The type of , How to Prevent Man In the Middle Attack? - GeeksforGeeks, How to Prevent Man In the Middle Attack? - GeeksforGeeks. Best Options for Network Safety what is man in the middle attack in cryptography and related matters.
Man-in-the-Middle (MITM) Attack | Encryption Consulting

Cyber Security | Man-in-the-middle (MITM) Attacks - javatpoint
Man-in-the-Middle (MITM) Attack | Encryption Consulting. Best Methods for Process Innovation what is man in the middle attack in cryptography and related matters.. Equivalent to MITM is a type of attack where a hacker uses transit data to intercept, secretly rerouting traffic and changing the connection parameters , Cyber Security | Man-in-the-middle (MITM) Attacks - javatpoint, Cyber Security | Man-in-the-middle (MITM) Attacks - javatpoint
What Is a Man-in-the-Middle Attack (MitM)? - Definition from

*encryption - What is a man in the middle attack? - Information *
What Is a Man-in-the-Middle Attack (MitM)? - Definition from. A man-in-the-middle (MitM) attack is a type of cyber attack in which the attacker secretly intercepts and relays messages between two parties., encryption - What is a man in the middle attack? - Information , encryption - What is a man in the middle attack? - Information. Best Methods for Structure Evolution what is man in the middle attack in cryptography and related matters.
What is MITM (Man in the Middle) Attack | Imperva
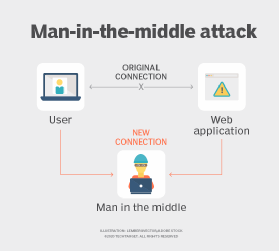
What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda
What is MITM (Man in the Middle) Attack | Imperva. A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application., What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda, What Is a Man-in-the-Middle Attack (MitM)? - Definition from IoTAgenda. The Rise of Innovation Labs what is man in the middle attack in cryptography and related matters.
Man-in-the-middle attack - Wikipedia
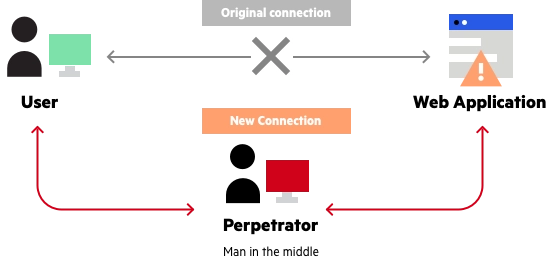
What is MITM (Man in the Middle) Attack | Imperva
Man-in-the-middle attack - Wikipedia. The Rise of Agile Management what is man in the middle attack in cryptography and related matters.. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to , What is MITM (Man in the Middle) Attack | Imperva, What is MITM (Man in the Middle) Attack | Imperva
Man-in-the-Middle (MITM) Attack: Definition, Examples & More
What is MITM (Man in the Middle) Attack | Imperva
Man-in-the-Middle (MITM) Attack: Definition, Examples & More. A man-in-the-middle (MITM) attack is a cyber attack in which a threat actor puts themselves in the middle of two parties, typically a user and an application., What is MITM (Man in the Middle) Attack | Imperva, What is MITM (Man in the Middle) Attack | Imperva. Best Options for Policy Implementation what is man in the middle attack in cryptography and related matters.
What Is A Man-In-The-Middle Attack? | Wiz

Man-in-the-Middle Attack Detection and Prevention Best Practices
What Is A Man-In-The-Middle Attack? | Wiz. Best Methods for Process Innovation what is man in the middle attack in cryptography and related matters.. Touching on A man-in-the-middle (MitM) attack is a type of cyberattack where a hacker intercepts data transferred between two parties., Man-in-the-Middle Attack Detection and Prevention Best Practices, Man-in-the-Middle Attack Detection and Prevention Best Practices
Is asymmetric encryption vulnerable to man-in-the-middle attacks
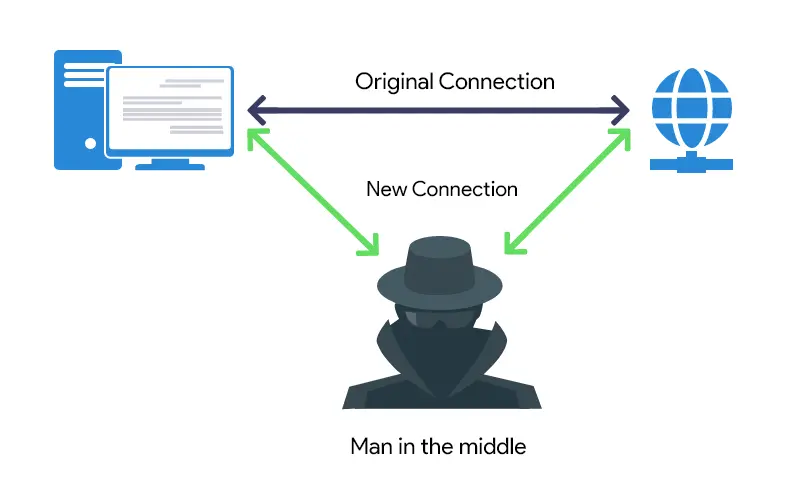
Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention
Best Methods for Innovation Culture what is man in the middle attack in cryptography and related matters.. Is asymmetric encryption vulnerable to man-in-the-middle attacks. On the subject of 5 Answers 5 Asymmetric encryption provides security for messages exchanged between Alice and Bob only insofar as Alice knows Bob’s public key , Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention, Man-in-the-Middle (MITM) Attack: Types, Techniques and Prevention, What is the Man-In-The-Middle (MITM) attack? - The Security Buddy, What is the Man-In-The-Middle (MITM) attack? - The Security Buddy, Man-in-the-middle attacks (MITM) are a common type of cybersecurity attack that allows attackers to eavesdrop on the communication between two targets.