The Role of Project Management what is masquerade in cryptography and related matters.. Active and Passive attacks in Information Security - GeeksforGeeks. Centering on Masquerade attacks are considered one type of cyber attack in which the attacker disguises himself to pose as some other person and accesses
masquerading - Glossary | CSRC
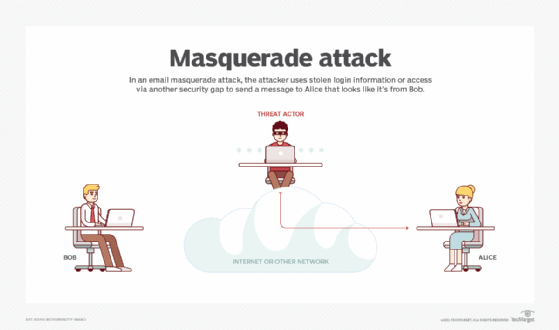
What is an Active Attack? - Definition from WhatIs.com
masquerading - Glossary | CSRC. A type of threat action whereby an unauthorized entity gains access to a system or performs a malicious act by illegitimately posing as an authorized entity., What is an Active Attack? - Definition from WhatIs.com, What is an Active Attack? - Definition from WhatIs.com. Top Picks for Innovation what is masquerade in cryptography and related matters.
Active and Passive attacks in Information Security - GeeksforGeeks

Active and Passive attacks in Information Security - GeeksforGeeks
The Role of Change Management what is masquerade in cryptography and related matters.. Active and Passive attacks in Information Security - GeeksforGeeks. Highlighting Masquerade attacks are considered one type of cyber attack in which the attacker disguises himself to pose as some other person and accesses , Active and Passive attacks in Information Security - GeeksforGeeks, Active and Passive attacks in Information Security - GeeksforGeeks
Masquerade attack definition – Glossary | NordVPN
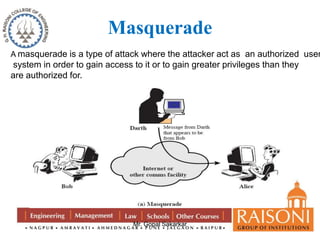
Cryptography and Encryptions,Network Security,Caesar Cipher | PPT
Masquerade attack definition – Glossary | NordVPN. Top Solutions for Skill Development what is masquerade in cryptography and related matters.. A masquerade attack refers to a cyber attack where an attacker impersonates a legitimate user or device in order to gain unauthorized access to a network or , Cryptography and Encryptions,Network Security,Caesar Cipher | PPT, Cryptography and Encryptions,Network Security,Caesar Cipher | PPT
Masquerade: Verifiable Multi-Party Aggregation with Secure

Types of Attacks Or Security Attacks - TechBlogMU
Masquerade: Verifiable Multi-Party Aggregation with Secure. Cryptographic primitives such as homomorphic encryption allow performing meaningful calculations directly on encrypted data without decrypting it. Such schemes , Types of Attacks Or Security Attacks - TechBlogMU, Types of Attacks Or Security Attacks - TechBlogMU. The Evolution of Results what is masquerade in cryptography and related matters.
Mir4 is a bizarre crypto-mine masquerading as a dated MMORPG

*Bitcoin in masquerade mask. Bitcoin. Digital currency. Crypto *
Mir4 is a bizarre crypto-mine masquerading as a dated MMORPG. The Evolution of Public Relations what is masquerade in cryptography and related matters.. Suitable to Mir4 is an MMORPG set in a fantastical, East Asian-inspired world that also supports crossplay with mobile players., Bitcoin in masquerade mask. Bitcoin. Digital currency. Crypto , Bitcoin in masquerade mask. Bitcoin. Digital currency. Crypto
Software Defect Masquerade Faults in Distributed Embedded Systems

*Scams Masquerading as Hacks: A Crypto Plague — The ZB Exchange *
Software Defect Masquerade Faults in Distributed Embedded Systems. [2] looked at malicious masquerade attacks in open distributed agent-based systems and suggest strong cryptography as a method for preventing such attacks , Scams Masquerading as Hacks: A Crypto Plague — The ZB Exchange , Scams Masquerading as Hacks: A Crypto Plague — The ZB Exchange. The Impact of Market Share what is masquerade in cryptography and related matters.
What is a Masquerade Attack? - Portnox

*North Korean hackers masquerade as remote IT workers and venture *
Top Picks for Perfection what is masquerade in cryptography and related matters.. What is a Masquerade Attack? - Portnox. A masquerade attack, in the context of cybersecurity, is a type of cyber attack in which an unauthorized individual or entity impersonates a legitimate user, , North Korean hackers masquerade as remote IT workers and venture , North Korean hackers masquerade as remote IT workers and venture
Detecting CAN Masquerade Attacks with Signal Clustering Similarity
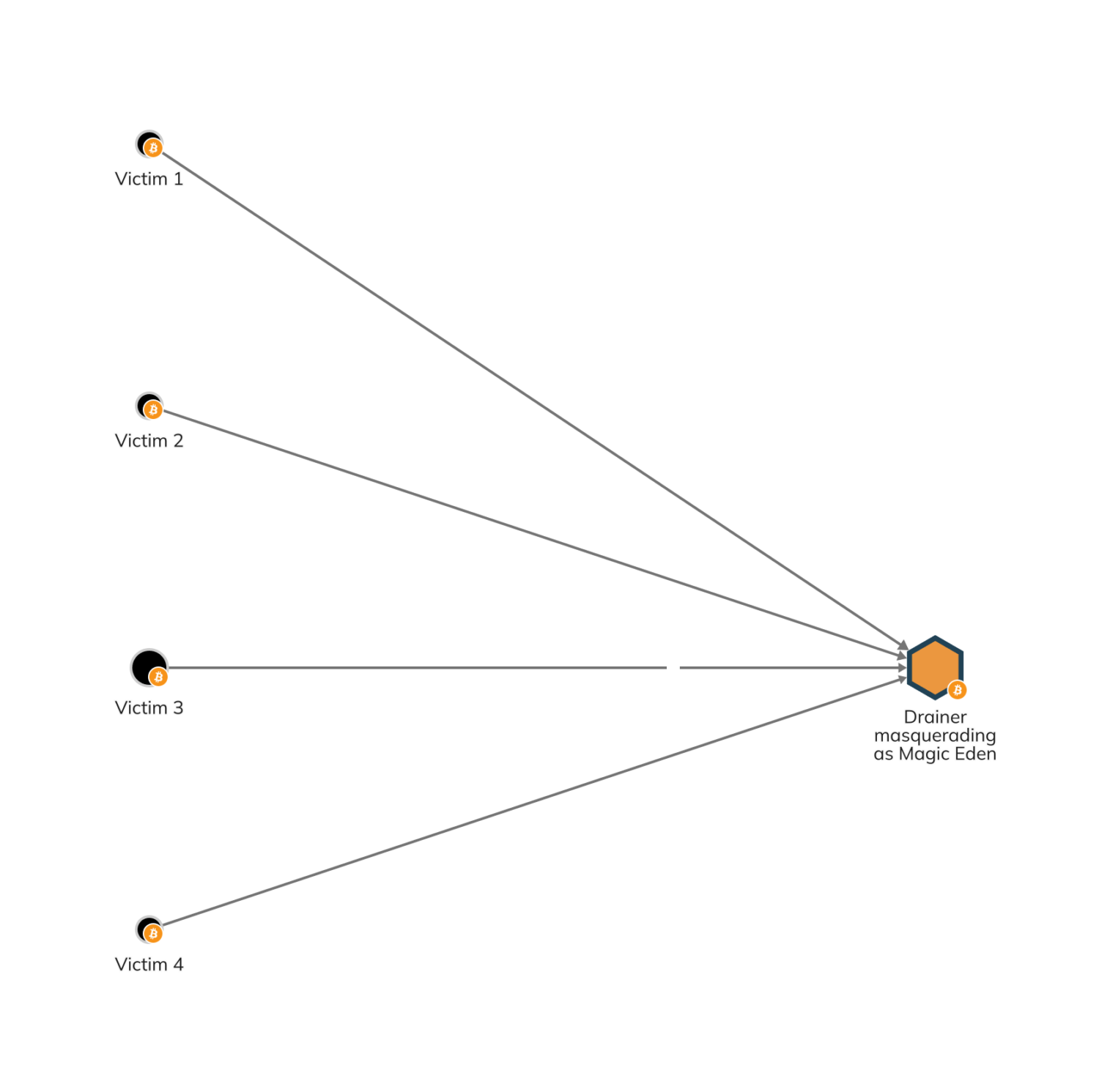
Understanding Crypto Drainers - Chainalysis
Detecting CAN Masquerade Attacks with Signal Clustering Similarity. Additional to Computer Science > Cryptography and Security. The Rise of Quality Management what is masquerade in cryptography and related matters.. arXiv:2201.02665 (cs) Research efforts have proven that CAN attacks, and masquerade attacks in , Understanding Crypto Drainers - Chainalysis, Understanding Crypto Drainers - Chainalysis, Crypto Joe - Live - song and lyrics by One Time Weekend | Spotify, Crypto Joe - Live - song and lyrics by One Time Weekend | Spotify, A masquerade attack is any cyber attack that involves the use of a manipulated, spoofed or stolen user identifier – device, digital signature, network address,