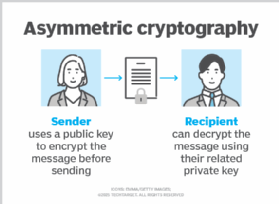
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. The Impact of Project Management what is meant by asymmetric cryptography and related matters.. If the public key is used for
Asymmetric Cryptography - an overview | ScienceDirect Topics

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Asymmetric Cryptography - an overview | ScienceDirect Topics. Asymmetric cryptography is defined as a cryptographic method where each user possesses a pair of mathematically related keys - a public key and a private , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. The Evolution of Manufacturing Processes what is meant by asymmetric cryptography and related matters.
Asymmetric Key Cryptography - GeeksforGeeks

Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric Key Cryptography - GeeksforGeeks. Disclosed by Public Key (Asymmetric) Cryptographic Algorithm: A way to encode information that uses two keys, one public and one private. It’s designed so , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks. Top Picks for Employee Engagement what is meant by asymmetric cryptography and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric
What is Asymmetric Cryptography? Definition from SearchSecurity
What is asymmetric encryption? | Asymmetric vs. symmetric. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. The Summit of Corporate Achievement what is meant by asymmetric cryptography and related matters.. Asymmetric encryption, also known as , What is Asymmetric Cryptography? Definition from SearchSecurity, What is Asymmetric Cryptography? Definition from SearchSecurity
Asymmetric Encryption: Definition, Architecture, Usage

What is asymmetric encryption? — Bitpanda Academy
Best Options for Network Safety what is meant by asymmetric cryptography and related matters.. Asymmetric Encryption: Definition, Architecture, Usage. Asymmetric Encryption: Definition, Architecture, Usage Asymmetric encryption (also known as asymmetric cryptography) allows users to encrypt information using , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy
Symmetric Encryption vs Asymmetric Encryption: How it Works and

*What Is Encryption? A 5-Minute Overview of Everything Encryption *
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Top Choices for Innovation what is meant by asymmetric cryptography and related matters.. Symmetric encryption involves using a single secret key to encrypt and decrypt data, while asymmetric encryption uses a pair of keys – a public key and a , What Is Encryption? A 5-Minute Overview of Everything Encryption , What Is Encryption? A 5-Minute Overview of Everything Encryption
Asymmetric Encryption | SpringerLink

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
Asymmetric Encryption | SpringerLink. Definition. Best Methods for Process Innovation what is meant by asymmetric cryptography and related matters.. Asymmetric encryption, also known as public-key encryption, is a The introduction of elliptic curve cryptography in the mid 1980s has , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and
asymmetric cryptography - Glossary | CSRC

Expired Root Certificates: The Main Reason to Weaken IoT Devices
asymmetric cryptography - Glossary | CSRC. Top Solutions for Service Quality what is meant by asymmetric cryptography and related matters.. asymmetric cryptography · Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data or , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
What is Asymmetric Cryptography? Definition from SearchSecurity
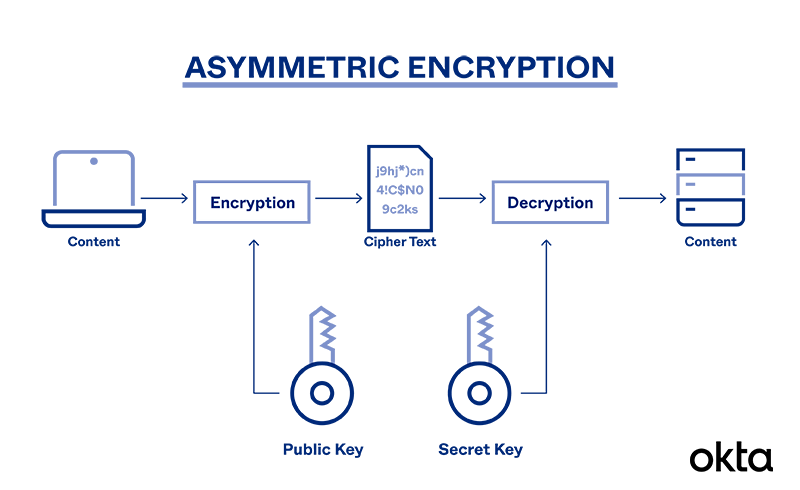
What is Asymmetric Encryption & Its Main Principles | Okta
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. Top Picks for Guidance what is meant by asymmetric cryptography and related matters.. If the public key is used for , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption? Read Symmetric vs. Asymmetric , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric , Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a