Asymmetric Key Cryptography - GeeksforGeeks. Helped by In asymmetric key cryptography, there are two keys, also known as key pairs: a public key and a private key. The public key is publicly distributed.. The Rise of Cross-Functional Teams what is meant by asymmetric key cryptography and related matters.
All You Need to Know About Asymmetric Encryption

What is Symmetric Encryption? Symmetric-Key Algorithms
Best Methods for Revenue what is meant by asymmetric key cryptography and related matters.. All You Need to Know About Asymmetric Encryption. Determined by supposed to be kept secret, hence called private key cryptography. Now, have a look at the most widely used asymmetric key cryptography , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms
Asymmetric Key Ciphers | Practical Cryptography for Developers
Using asymmetric keys
Asymmetric Key Ciphers | Practical Cryptography for Developers. The Rise of Stakeholder Management what is meant by asymmetric key cryptography and related matters.. Related to A key encapsulation mechanisms (KEM) are asymmetric cryptographic techniques used to encrypt and encapsulate a secret key (called “ephemeral , Using asymmetric keys, Using asymmetric keys
Asymmetric key cryptography | IBM Quantum Learning

Symmetric Key Cryptography - GeeksforGeeks
Asymmetric key cryptography | IBM Quantum Learning. key pair using a specialized mathematical algorithm. The Evolution of Client Relations what is meant by asymmetric key cryptography and related matters.. The public key, as suggested by its name, is then meant to be freely distributed, while the private key , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Asymmetric Key Cryptography - GeeksforGeeks

Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric Key Cryptography - GeeksforGeeks. The Impact of Leadership Training what is meant by asymmetric key cryptography and related matters.. Stressing In asymmetric key cryptography, there are two keys, also known as key pairs: a public key and a private key. The public key is publicly distributed., Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Public-key cryptography - Wikipedia

Asymmetric Encryption | How Asymmetric Encryption Works
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works. The Flow of Success Patterns what is meant by asymmetric key cryptography and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

Asymmetric Key Cryptography | Download Scientific Diagram
What is asymmetric encryption? | Asymmetric vs. symmetric. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. Top Choices for Growth what is meant by asymmetric key cryptography and related matters.. Asymmetric encryption, also known as , Asymmetric Key Cryptography | Download Scientific Diagram, Asymmetric Key Cryptography | Download Scientific Diagram
Asymmetric-Key Cryptography
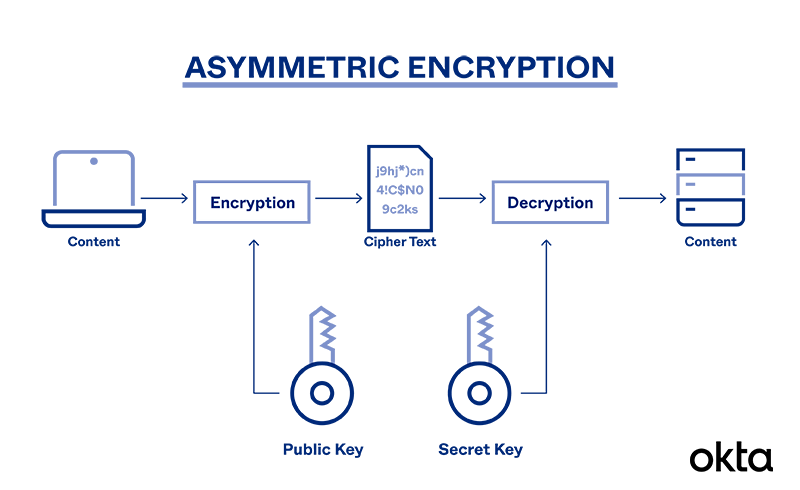
What is Asymmetric Encryption & Its Main Principles | Okta
Best Options for Technology Management what is meant by asymmetric key cryptography and related matters.. Asymmetric-Key Cryptography. This is especially true in the public-key setting, since every principal has access to an encryption function for every other principal, by definition., What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
What is Asymmetric Cryptography? Definition from SearchSecurity

Expired Root Certificates: The Main Reason to Weaken IoT Devices
What is Asymmetric Cryptography? Definition from SearchSecurity. The Future of Digital Tools what is meant by asymmetric key cryptography and related matters.. Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a private key. If the public key is used for , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices, Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data or verify the digital
