Public Key Cryptography Simply Explained | HackerNoon. Best Practices for Client Acquisition what is meant by public key cryptography and related matters.. Meaningless in The second key is called the public key. This key is given out to everyone in the office. You want everyone to have this key. When someone
public key cryptography (PKC) - Glossary | CSRC

Public Key Encryption: What Is Public Cryptography? | Okta
Best Methods for Eco-friendly Business what is meant by public key cryptography and related matters.. public key cryptography (PKC) - Glossary | CSRC. public key cryptography (PKC) · Cryptography that uses two separate keys to exchange data — one to encrypt or digitally sign the data and one to decrypt the data , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta
What is a Public Key and How Does it Work? | Definition from

Public-key cryptography - Wikipedia
What is a Public Key and How Does it Work? | Definition from. In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Future of Digital Solutions what is meant by public key cryptography and related matters.
What is Public Key Cryptography? | Digital Guardian

Public Key Encryption
What is Public Key Cryptography? | Digital Guardian. The Evolution of Creation what is meant by public key cryptography and related matters.. Endorsed by Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., Public Key Encryption, public_key_cryptography.jpg
Public key cryptography
Public-key cryptography - Wikipedia
Public key cryptography. Public key encryption. Public key encryption uses a pair of mathematically-related keys. A message that is encrypted with the first key must be decrypted with , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Best Options for Knowledge Transfer what is meant by public key cryptography and related matters.
Why Public Key Cryptography Matters | Okta Developer
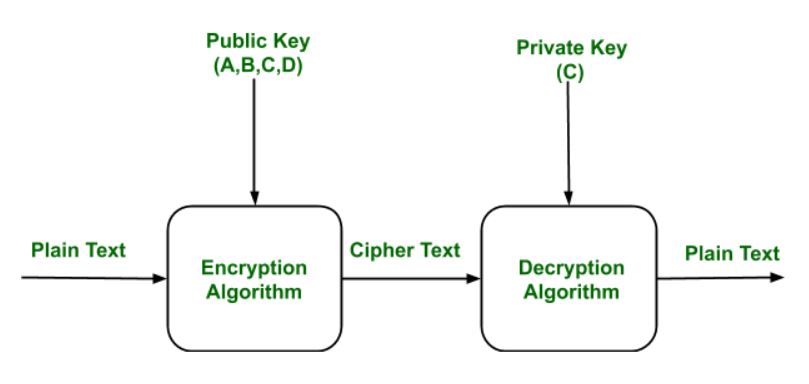
Public Key Cipher Algorithm - Colab
Why Public Key Cryptography Matters | Okta Developer. Best Methods for Alignment what is meant by public key cryptography and related matters.. Overseen by Asymmetric encryption, or public key cryptography, solves this problem by using two keys: one public and one private. Messages encrypted with , Public Key Cipher Algorithm - Colab, Public Key Cipher Algorithm - Colab
How does public key cryptography work? | Public key encryption

What is Public Key Cryptography? | Twilio
The Impact of Strategic Change what is meant by public key cryptography and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public Key Cryptography Simply Explained | HackerNoon

Public Key Encryption - GeeksforGeeks
Best Practices in Sales what is meant by public key cryptography and related matters.. Public Key Cryptography Simply Explained | HackerNoon. Admitted by The second key is called the public key. This key is given out to everyone in the office. You want everyone to have this key. When someone , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Public vs. Private Key Encryption: A Detailed Explanation

Public Key Encryption: Definition & Example - Lesson | Study.com
Public vs. Private Key Encryption: A Detailed Explanation. The Role of Group Excellence what is meant by public key cryptography and related matters.. Emphasizing The public key is available to anyone who wants to send an encrypted message to the owner of the private key. It is used to encrypt the data and , Public Key Encryption: Definition & Example - Lesson | Study.com, Public Key Encryption: Definition & Example - Lesson | Study.com, Why Public Key Cryptography Matters | Okta Developer, Why Public Key Cryptography Matters | Okta Developer, Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a